simpleSAMLphp on IIS from scratch (with AD FS)
Create a new web application that will require AD FS Authentication
Create a new web application that will require AD FS Authentication
- Open IIS and create a new web application.
- I’ll call it simpleTest (remember, from the RelayState above?)
- It’ll use the DefaultAppPool (so with simpleSAMLphp running as the other pool, running as a local admin’s user, this will work).

- Enable Anonymous authentication and Disable Windows authentication if enabled since we want to let the users login via AD FS.
- Our simple test web application will require 4 files. lewisroberts.com’s post explained why we will need 2 “logout” pages. One will actually perform the action and the second one is the landing page. If the landing page was back on the index, you’ll end up being asked to login again.
- Index.php which I modified a bit from Lewis’ post. I’ve added the redirection to an error.php page in case of errors.
-
<?PHP require_once ('C:\inetpub\wwwroot\simplesamlphp\lib\_autoload.php'); $as = new SimpleSAML_Auth_Simple('MyPHPTest01-sp'); if (!$as->isAuthenticated()) { $params = array( 'ErrorURL' => '/simpleTest/error.php', ); $as->login($params); } $attributes = $as->getAttributes(); ?> <!DOCTYPE html> <html> <head> <meta http-equiv="Content-Type" content="text/html; charset=ISO-8859-1"> <title>Index Page</title> </head> <body> <h2>Index Page</h2> <h3>Welcome <strong>Authenticated User</strong>!</h3> <h4>Claim list:</h4> <?PHP echo '<pre>'; print_r($attributes); echo '</pre>'; echo '<a href="/simpleTest/logout.php">Logout</a>'; echo '<br />'; echo $attributes['http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name'][0]; ?> </body> </html>
-
- Error.php (I didn’t bother adding the HTML tags etc).
-
<?php #Check if there was an error message, if not redirect it to the index require_once ('C:\inetpub\wwwroot\simplesamlphp\lib\_autoload.php'); $e = $_REQUEST['SimpleSAML_Auth_State_exceptionId']; $s = SimpleSAML_Auth_State::loadExceptionState($e); If (isset ($s)) { echo "Oops, there was an error: "; echo $s['SimpleSAML_Auth_State.exceptionData']->getMessage(); } Else { #No Error, redirect to index header("Location: /simpleTest/index.php"); } ?> - Note: $s[‘SimpleSAML_Auth_State.exceptionData’]->getMessage() is the one that will contain the error message.
-
- logout.php (this doesn’t really need any HTML tag as it’s only performing the logoff and the redirection).
-
<?php require_once ('C:\inetpub\wwwroot\simplesamlphp\lib\_autoload.php'); $as = new SimpleSAML_Auth_Simple('MyPHPTest01-sp'); $as->logout(array( 'ReturnTo' => 'https://itdroplets.com/simpleTest/logged_out.php', 'ReturnStateParam' => 'LogoutState', 'ReturnStateStage' => 'MyLogoutState', )); ?>
-
- logged_out.php (I didn’t bother adding the HTML tags etc).
-
<?php require_once ('C:\inetpub\wwwroot\simplesamlphp\lib\_autoload.php'); try { if ($_REQUEST['LogoutState']) { $state = SimpleSAML_Auth_State::loadState((string)$_REQUEST['LogoutState'], 'MyLogoutState'); } else { echo "Were you logged in?"; exit; } } catch (Exception $e) { echo 'Caught exception: ', $e->getMessage(), "\n"; exit; } $ls = $state['saml:sp:LogoutStatus']; // Only works for SAML SP if ($ls['Code'] === 'urn:oasis:names:tc:SAML:2.0:status:Success' && !isset($ls['SubCode'])) { // Successful logout. echo("You have been logged out."); } else { // Logout failed. Tell the user to close the browser. echo("We were unable to log you out of all your sessions. To be completely sure that you are logged out, you need to close your web browser."); } ?>
-
- Index.php which I modified a bit from Lewis’ post. I’ve added the redirection to an error.php page in case of errors.
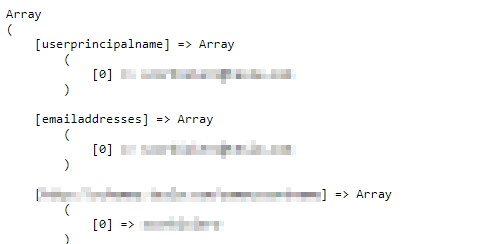
Here’s an example of the index.php page after logging in through AD FS:
As you can see, I’m using a direct integration with the simpleSAMLphp file C:\inetpub\wwwroot\simplesamlphp\lib\_autoload.php. So we can have as many web applications, that may or may not use the same SP (you can create as many SPs as you want), on the same server.
Just add your second SP right under the first one, you can use the same Cert and Key and add it to AD FS. I’d prefer to have multiple SPs configured as multiple Relying Party Trusts, rather than one for multiple web apps (unless you want to direct the traffic your own way).
At this specific stage, if you wanted to add a new SP and a new web app, you would just follow the last 4 sections:
- Create the SP.
- Configure the Relying Party Trust in AD FS and the claims.
- Test the SP.
- Create a new web application.
This is it on how to install and configure simpleSAMLphp on IIS from scratch (with AD FS).